04 Jan The New Pirates of the Sea
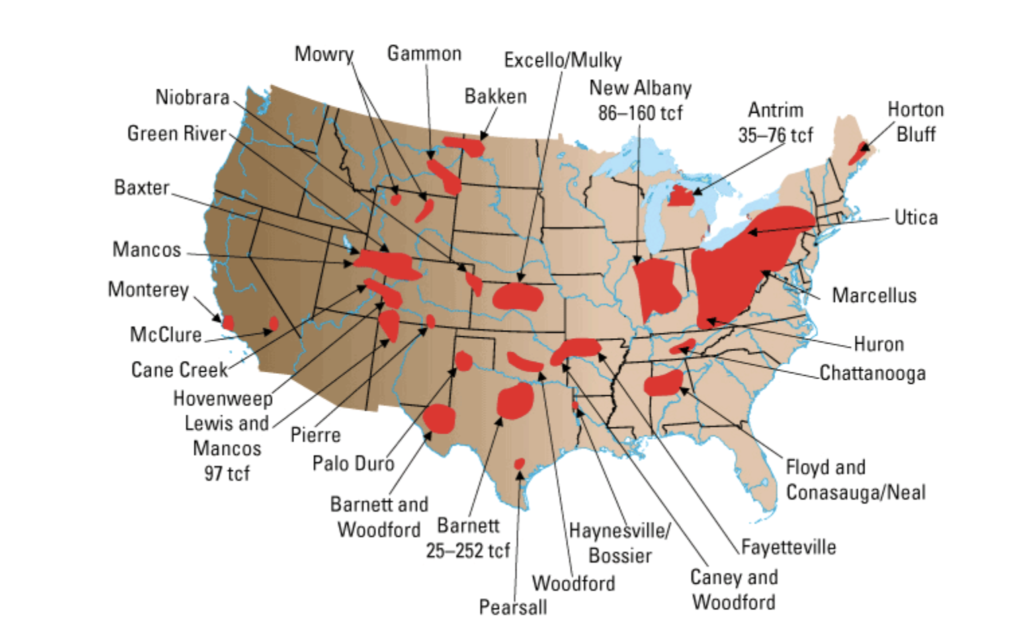
North America is blessed with at least twelve beautiful underground seas of a different sort; these seas are invisible from above and are deep blue vaccous pools wedged between shale rock. These Shale beds carry with them the tides of fiscal and natural resource bounty, U.S. energy independence and a promise of a much brighter economic future. What also comes along for the ride are the vicarious ups and downs driven by complex corporate, environmental, social and manufacturing responsibilities involved with the various stages of the work in this sector. Exploration, mining, transport, break down and use of this valuable resource we call wet and dry natural gas, is nothing short of highly complex, highly regulated and highly susceptible to risk of all kinds. Further, there is no shortage of opinions and commentary regarding these risks.
In fact, mainstream society has experienced such an increase of new awareness regarding this sub culture of science and language, the topic of hydraulic fracturing has been at the center of many discussions and debates on all sides of every imaginable political aisle. Said a different way, do we ever recall a time when fracturing (fracing), cracker (ethylene) plants, wet gas (Utica), dry gas (Marcellus), shale beds, down –holesmen , ‘camps’ (drill sites) or greenfields (newly laid pipeline routes) meant something other than what we grew up learning? Or has there ever been another time in local history where upper middle and lower stream meant something other than where the fish were biting that month? These terms and their new meanings have worked their way into the corporate water cooler talk too; it’s almost as if the whole free world is entitled with PE after their name or is a Geologist by trade.
Popular Discussion
Actually, the discussion of managing risk within energy exploration- especially natural gas exploration via the process of hydraulic fracturing (fracing) truly is of the utmost populous discussions in this invariably protracted and complex sector involving the Shale boom. To that end, there has been a literal tidal wave of activity surrounding the reporting of US Natural Gas Exploration and Energy Independence that has hit media platforms with full force. One can hardly pick up a paper or turn on a TV without exposure to multiple myriads of both political and factual media stories of such highly technical activities like fracturing, geological rock formation, compressed and liquid gas blow-out capability and many other complex topics. This is especially true for those living and working in Ohio, Pennsylvania and West Virginia. In this Appalachian Region, the names Marcellus and Utica have become almost as familiar as their western and southern second cousins, who are named Bakken and Barnett.
Background
There is very good reason for very visceral discussion on Energy related topics here in the United States; figures released from 1Q 2014 cite the US as the largest world oil producer to the tune of 11m bbl per day in just the first three months of the year (Anthony Albanese, June 2014). Because of this and many other business reasons, this heightened level of national energy independence and local Marcellus and Utica Shale activity are not only common table talk but are also common key corporate strategic and business planning initiatives, as well. The technicalities of this dynamic and evolving energy sector continue to change and develop daily. As well, the fiscal nature of this business is literally exploding at the same time. And with this type of subject complexity and revenue value, it is clear why all things Shale are topics fraught with diverse and ardent opinions.
Known Risks
Further, while there are many real and intangible hazards along the road of supply chain management in this evolving sector, everyone can agree on certain inherent risk truths regarding the energy sector in general. These common grounds of agreement include the salient need to properly identify, anticipate, manage and mitigate all things risk when it comes to all things Shale. Some of the commonly identified risks include human capital issues, protecting the environment, handling business interruption/supply chain risk, dealing with explosion and fire or theft, patent infringement, reputation protection or general liability are not the only possible navigable hazards in this new found sea of blue.
As a matter of fact, the typical claims catastrophes initially thought of in critical risk management discussions, are actually trending down. In the 2014 Market Realities report and according to internal Willis global energy claim tracking, Upstream claims in 2013 recorded only two losses in excess of 200 million U.S. dollars. Further, on the Downstream side, despite the fact there were three serious accidents in Argentina, the U.S.A and Canada, the loss record is actually improving as the catastrophes of 2011 begins fade from contractual liability claims reserves and payments.
The New Pirates
However, there are a few more insidious (and costly) threats along this horizon that are hidden, peculiar and unique, and who get very little air time. They rear their ugly heads infrequently but when they do, the silence of their stealth style of compromise has already rung the biggest bell for losses in the shortest amount of time; they are responsible for stealing more from this industry than any of their aforementioned peers. What we are talking about are the real Pirates of the Blue Gas Sea- Cyber Crime, IT failures and Espionage. Of those, Cyber Crime issues are on the rise and among the stealthiest of offenders of risk management for any organization involved in this field. For that reason, Cyber Crime awareness is the main topic of this article and wins the award for biggest Pirate of the Shale Blue Sea.
For example, Global estimates that measure costs of cyber-attacks against oil and gas companies will cost this Industry nearly 2 billion dollars by 2018. Here in the United States, in 2012, a whopping 40% of all cyber-attacks on crucial infrastructure assets occurred against the Energy sector. In Europe, the government estimates that okl and gas companies already lose approximately 400m(GBP) a year as a result of cyber-attacks. Further, the Center for Energy Economics said there are 14 new ethylene crackers projects planned – five new plants, and nine expansions – worth a combined $26 billion in investments through 2020.
Furthermore, now that connectivity to the internet is so often the norm for so many Industrial Control Systems (ICSs) used by the energy industry, we can state that a major energy catastrophe- on the same scale as Piper Alpha, Phillips Pasadena, Exxon Valdez or Deepwater Horizon- could indeed be caused by a cyber-attack. Ironically, the Cyber-Attack may also be politically motivated, which even further increases the need to not only manage the risk but insure for protection of rights to recover for the loss.
Stuxnet
Meet a virus named Stuxnet. Stuxnet is the name of a computer virus discovered in June 2010 that was specifically designed to attack Siemens Step7 software running on a Windows operating system. Stuxnet ruined almost 20% of Iran’s uranium enrichment centrifuge capability by spinning out of control while simultaneously replaying the recorded system value which showed the centrifuges functioning normally during the attack. Stuxnet was also capable of downloading proprietary process information.
Night Dragon
Another new name to the Energy Sector is the virus Night Dragon. Attackers using several locations in the Asia Pacific region leveraged servers in the U.S and Western Europe to wage cyber-attacks against the global oil gas and petrochemical companies, as well as individuals and executives in Kazakhstan, Taiwan, Greece and the U. S. A.
Flame
A second example is Flame also known as Flamer, sKyWIper and Skywiper. This is a modular computer malware discovered in 2012 that attacks computes running the Microsoft Windows operating system. The program continues to be used for targeted cyber espionage in Middle Eastern countries.
Shamoon
The third example is actually a modular computer virus being used for cyber espionage in the energy sector and is one of the most prolific. This virus has been noted as unique because it has differing behaviors from other malware cyber espionage attacks and is capable of spreading to the other computers on a network. IT does this thru exploitation of shared hard drives. This virus launched in August 2012 and particularly effected major energy companies in the Middle. While no resulting damage happened, the virus was successful in orchestrating a shutdown of 30,000 computers belonging to a major state owned energy company on an unprecedented scale, destroying hard drives and data with a considerable loss of data and productivity.
Doqu
A final example is the Doqu virus which is a collection of computer malware discovered on September 1, 2011 and thought to be related to the Sutxnet worm. The destructive capabilities of Doqu have yet to be fully understood or measured. Doqu tainted files are recognizable because the virus assigns the prefix of ‘-DQ’ to every file it creates.
Vulnerabilities
According to lead Insurance Underwriters from companies like Hiscox, Kiln, Talbot, AIRMIC and Novae, companies must be aware of rogue employees, rogue environmental lobbyists, foreign and domestic competitors and politically motivated attackers. Further, Companies are hard-pressed to cut costs; sometimes without meaning to, these efforts can compromise the Cyber Security on a much larger scale than the initially calculated cost savings. For example, one popular way to do reduce costs and increase supply chain efficiency is to integrate certain Industrial Control Systems (ICSs). These include common systems like Supervisory Control and Data Acquisition Systems (SCADAs) and Distributed Control Systems (DCSs).
While these systems have done well to improve efficiencies and to allow management to view the volumes of data in real time, this type of seemingly innovative development has increased the possibility of oil and gas infrastructure being opened to a Cyber – Attack. In essence, too many control systems remain internet facing and modern energy facilities are designed to shut down safely in the event of a loss.
Another inadvertent way companies leave an unmitigated risk on the table and vulnerable to Cyber-Attack involves operations within Mobile Offshore Drilling Units (MODUs). The MODU control unit system and the IT data network that runs it is separated by an air gap which allows the control system to be unaffected by any malware infecting the data network. However, Control System security expert Christopher Goetz for Kinston Systems recently pointed out in the Digital Energy Journal mazing that this ‘air gap’ on many MODU’s is dissipating.
Further, this is leading to more external access points being introduced and further integration between the networks and disparate control systems, As well, further dependability on contractors to carry out work on the MODUSs means employing personnel who may be highly trained but not highly security controlled or in-company vetted.
Combating the Enemy
This issue of a Cyber-Attack on the US Shale and Energy plays is so prevalent that the United States Securities and Exchange Commission now provides specific guidance notes about the level of Cyber Risk disclosures that should be considered in fulfilling disclosure implications mandated by federal securities laws. It will not be surprising if the U.K. follows similar suit. This is an issue globally and the Shale play is a global venture. The embittered controversies, fierce competitive marketplace and enterprising data pirates are not going away any time soon. Because of this, the risk management field to protect companies from this malicious behavior is changing at a rapid pace and is developing with the times. As in all business sectors, the risk involved with the Energy sector can be mitigated by utilization of various insurance policies and key endorsements that can be aligned with the spedific risks involved with each operation risk attempting to be mitigated.
Currently, there are six key parts to well-rounded Cyber insurance market coverage.
Part 1: First Party Network Loss. This coverage will provide coverage for damage to digital assets affected by an attack, including the costs to recollect, recreate and reconstitute the digital assets of the company which are damage, lost, altered, corrupted, distorted or stolen. Coverage is also provided for income loss and interruption expenses incurred by the company during the period of resulting network downtime as a result of the attack. However there is no coverage for any physical loss or damage from the attack.
Part 2: Privacy and Security Liability. This covers damages and legal fees as a result of a privacy breach or breach of confidence. This also covers Third Party damages and legal fees as a result of unauthorized use/access, the transmission of a virus, and denial of service attacks as well as other computer crime.
Part 3: Media liability. This will pay for damages and legal fees as a result of a wrongful act in the course of publishing content in electronic or print media, including online social media platforms.
Part 4: Privacy Regulations Defense and Awards and Fines. This is coverage for expenses resulting from investigation adjustment, defense and appeal of regulatory proceedings, as well as privacy regulatory fins and penalties (where insurable by law).
Part 5: Crisis Management and Reputational Expenses. This coverage is available for costs to employ specialist forensic experts and solicitors to investigate and respond to a privacy breach or system failure. The policy will also pay for costs to notify victims of privacy breaches and provide them with identify theft assistance and costs for PR related services to mitigate reputation harm.
Part 6: Cyber Extortion. This coverage is available for costs involved in engaging crisis management experts, as well as the costs involved in paying ransoms (if deemed necessary).
Conclusions
As with any dynamic and constantly evolving commercial risk sector, Energy and all things Shale is a dynamic market force; there is little room for doubt or disappointment when it comes to the discovery, independence, fiscal wealth and scientific breakthrough engineering patents that will come from this new type of activity here in the United States and around the globe. It has also been a new and exciting field for Risk Managers and Actuaries to understand evaluate and keep up with current trends.
The key is for individuals and companies to properly identify risk, plan for it and be aware of the new Pirates along the deep seas of blue bounty found far below the ground we stand upon. Corporations can stay ahead of the curve when it comes to proactively thinking ahead to potential vulnerabilities and key sensitive areas of the manufacturing and procurement chain, confidential to that company. They can do this in a variety of ways at their annual Risk Review Meetings when selecting risk management expenditures. Truly, there has probably never been a better time to employee experienced critical risk aware leaders who can creatively and quietly keep ahead of the conniving and capable acts of the invisible Cyber Pirates the Energy industry wards off daily. Finally, there also has been no more salient of an issue such as discussed here, for sector leading Companies to support inter-Sector and cross-Company strategic thinking groups to share knowledge an thus enhance success rates against these silent but formidable types of attacks on a growing and dynamic industry.
Darlyn McDermott, MAOL, AINS, CLF, CLP II is an Energy producer at Willis, NA of Cleveland, Ohio. These are her views and not necessarily those of Willis, NA.
She has worked in Risk Management and Casualty Insurance for the past 21 years. The past 6 of those years have been involved with handling Risk Management for a variety of public and private entity classes including: Energy, commercial municipalities (Cities, Townships, Boroughs and Villages), Manufacturing, Transportation and Trucking, Fluid Milk and Recyclers. She was responsible for creating Keystone Shale Solutions and has led multiple industry discussions on the topic of MSA compliance and Risk Management at all levels of the supply chain. She is also a Green Belt in Six Sigma process improvement and will complete her Doctoral degree in 2016.
Darlyn A. McDermott, MAOL, CLF, AINS, CLPII
Willis of Ohio
1001 Lakeside Ave. Suite 1600, Cleveland Ohio 44114
Direct: +216 357 2824, Mobile: +330 858 5581 [email protected]
See what we stand for and how we serve our clients at www.willis.com/williscause
[email protected]
LinkedIN
Twitter: @darlynmcdermott
W (216) 357- 2824 and © 330 858- 5581
Willis
Willis is one of the world’s leading risk management and insurance intermediaries. We evolved by building our advisory and transactional capabilities into a worldwide, knowledge-based professional services organization. Willis is a global insurance broker; that’s all we do. Our 17,000 professionals in more than 400 offices spread across 120 countries are able to channel all of their energies into meeting our goal of being the world’s best insurance broker. Through our vast array of global resources, we are able to draw upon the talents and information found in any Willis office worldwide to consistently deliver to clients everywhere the expertise, products, and services they require and expect from us.
Willis was the first broker to form an intercontinental, multidisciplinary business unit servicing the energy industry on a global basis.
Willis’ Energy team services over 300 oil & gas accounts every year with combined premiums in excess of $1 billion, and our claims teams handle over 7,000 claims per year. We service every aspect of the energy industry from exploration and production to refining, from construction to manufacturing, from independent oil companies to service and drilling contractors.
Willis’ Houston office serves as our hub for the energy industry in North America and has over 150 employees, 50 of those employees are dedicated solely to the energy and marine sectors. Our Field Producers work closely with us and we support their clients. We are dedicated to service, as evidenced by our client retention rate of around 97%. We believe we are the best and most capable broker to cater to the energy industry. Our team of experts is ready to assist with all aspects of risk management strategies, consulting and insurance needs, including extensive contract and policy wording review and recommendations using our in-house legal team.



Sorry, the comment form is closed at this time.